We use Pulumi with TypeScript for our Infrastructure as Code. Why Pulumi instead of the more popular Terraform? Webiny uses it (see: why Webiny chose Pulumi?; Benefits of moving from Terraform to Pulumi), and since we’ll be using Webiny, it’s more natural to just use Pulumi also.
- cloud infrastructure is defined via code (TypeScript)
- it supports multiple cloud providers (AWS, Azure, Google Cloud Platform, …)
- it provides multiple solutions for storing infrastructure state
- a vibrant and rising community
Oct 15, 2021 reconsideration: CDK for Terraform, but it says “CDK for Terraform is an early experimental project and the development team would love your feedback to help guide the project.” Conclusion: Pulumi is still more practical.
Preparations
Pulumi Cloud: Sign up for Pulumi Free Account
Sign up at https://app.pulumi.com/
Note: Pulumi provides choices to store the infrastructure state: 1) Pulumi Cloud (easiest), 2) Local .pulumi/ folder inside project folder, 3) S3. For now, we use Pulumi Cloud with a single shared account.
Install Pulumi on Ubuntu
curl -fsSL https://get.pulumi.com | shTo make PATH changes take effect, close Terminal and relaunch Terminal.
Pulumi with TypeScript Tutorial
pulumi new
# choose aws-typescriptpulumi up -s stagingImporting Existing AWS Infrastructure
https://www.pulumi.com/docs/guides/adopting/import/
Pulumi and Soluvas AppStudio
Pulumi will be naturally useful to Soluvas AppStudio.
Providers
AWS Provider
TODO
Cloudflare Provider
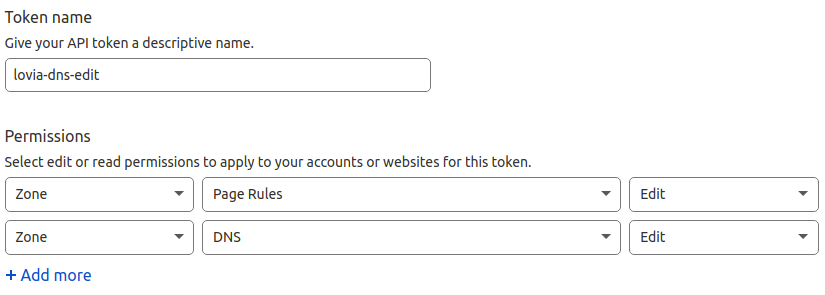
The required permissions for Cloudflare token are: Zone – DNS – Edit, and Zone – Page Rules – Edit.
Security Consideration: Secrets
- Never store secrets in a Pulumi stack configuration and/or state! Secrets must always be externalized to a secrets manager (e.g. AWS SSM Parameter Store)
- If a secret/password is unavoidable to be put in Pulumi state, use the following technique instead:
- In Pulumi, put a placeholder (not the real secret) as initial secret/password, then use
ignoreChangesto ignore changes on the secret/password - Using Ansible, create the secret, put it on AWS SSM Parameter Store, and set it as the new secret
- At this point the secret stored in Pulumi state will be “useless” (it’s stale and will never be used too)
- In Pulumi, put a placeholder (not the real secret) as initial secret/password, then use